Passwords have been used for decades, but today they are one of the weakest links in security. Many people reuse passwords, choose easy ones, or lose them to phishing attacks. Passkeys offer a safer alternative by removing passwords entirely and using secure device-based authentication instead.
Read MoreCyberthreats are growing every day, and password leaks have become increasingly common.
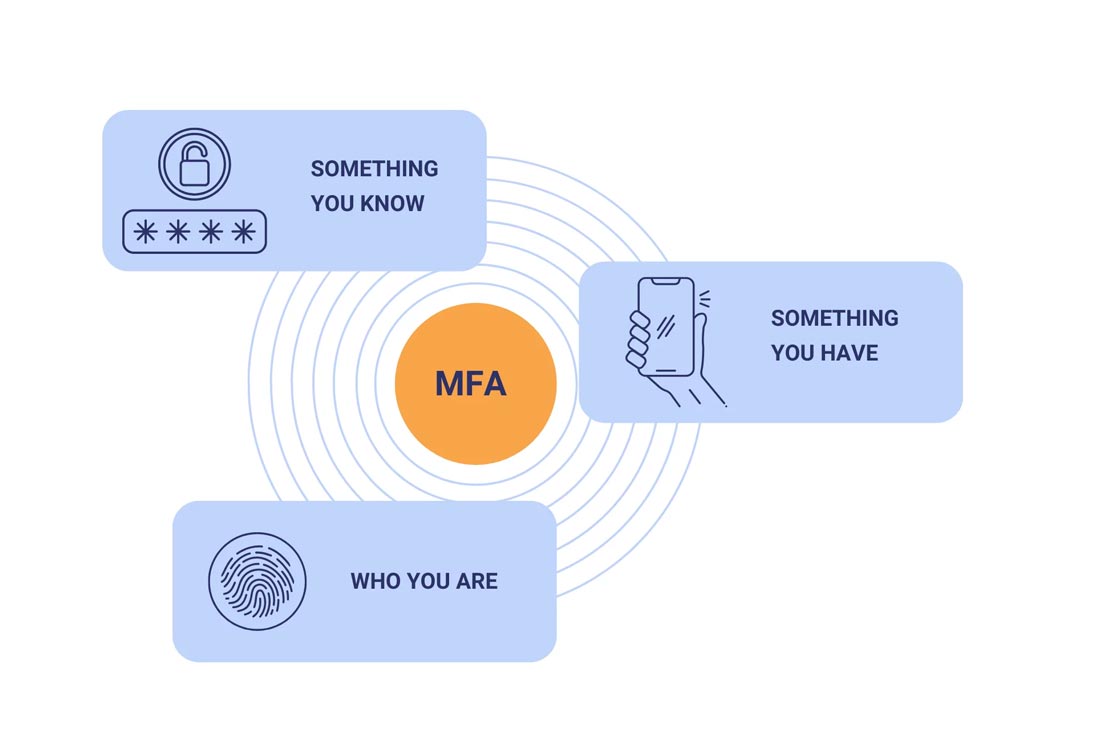
Enabling multi-factor authentication (MFA) adds a critical extra layer of protection beyond passwords alone.
WhatsApp works constantly to protect users from spyware and other harmful attacks. The platform uses strong privacy and security tools to keep your messages and calls safe. One of the most important tools is end-to-end encryption.
Read MoreMicrosoft has officially announced that Windows 10 reached its end of support on October 14, 2025. This marks the end of security updates,
DeepSeek AI, a prominent Chinese artificial intelligence startup, has rapidly emerged as a significant player in the global AI landscape.
Read More